vSphere with Tanzu Supervisor Services Part III - Lifecycle Management of Supervisor Services
Recap and Intro
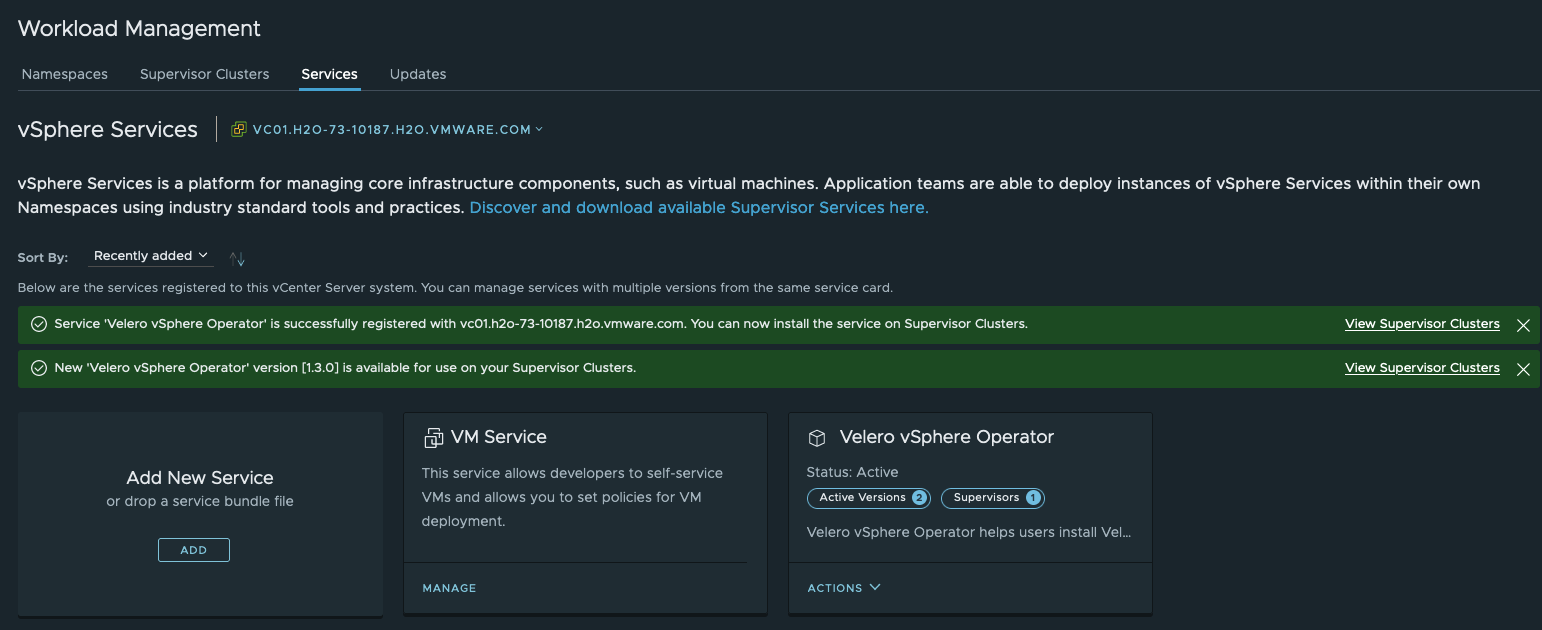
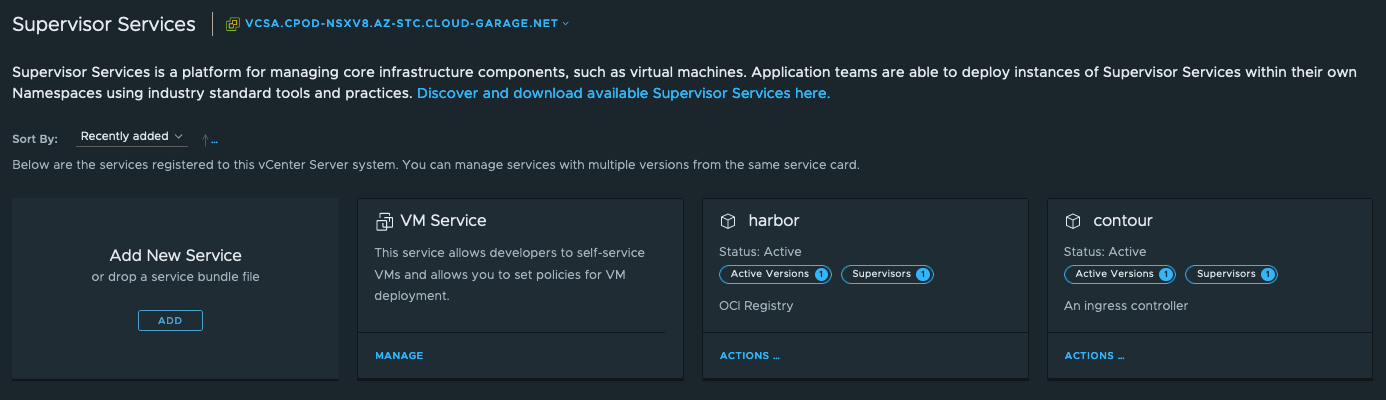
In Part I and II of my blog series on the Supervisor Services in vSphere with Tanzu (TKG with Supervisor Model), I covered the topics from registering and installing a new service on a Supervisor Cluster until how to leverage a service for functionalities like e.g. hosting container images (Registry Service) or handling incoming traffic (Ingress Service) for vSphere Pod based applications.